If your pentester can break into your mobile app by means of a vulnerability, you wager that a real hacker should be able to do the exact same. This presents your crew With all the evidence it needs to pinpoint the specific places to put into practice the right application security controls essential to successfully shield the mobile app atmosphere. The reasonable mother nature of the results garnered from black box pentesting signifies that the organization can get a far more sensible notion regarding what an everyday penetration assaults would do to their Firm.
Heather: Mobile forensics is rapid-relocating. Mobile device businesses update devices and functioning methods constantly. The purposes we rely upon are updating.
Communication and documentation are essential competencies for penetration testers. Within a pentesting engagement, Just about every step of the method ought to be Plainly documented for the advantage of each the pentester plus the customer. If anything breaks or malicious activity is detected inside the natural environment, the pentester requires to be able to verify that they didn't do anything at all outside the agreed-upon procedures of engagement.
And for those worried about the scamming aspect of a hire-a-hacker website, resources for a selected work is usually held in escrow to make certain They are only paid out out upon its completion. Hacker's List promises that it's a "focused dispute procedure" in place to manage challenges between events, should they occur.
If You are looking for the most effective security services in existence, you've come to the best put. At Penticians, we pride ourselves on getting the ideal in the enterprise.
The important thing to fixing a electronic security issue is TIME . The quickest reaction often will get the very best consequence.
Black hat Website positioning – the hacker will change online search engine effects to spice up or reduce a internet site’s rankings. (Writer’s Take note: I was shocked we didn’t see much more of those).
Ensure that everyone in your organization involved with the process is prepared to act on the outcome quickly. Consider scheduling a meeting While using the committee when you receive the report.
Hacking for Dummies: This book introduces novices to critical ideas surrounding safeguarding data and approaches to if not prevent cyber criminals.
Obviously, not only everyone can call on their own a pacesetter in Hacking. There exists a sure level of skill and expertise needed.
He is usually the creator of over a dozen cybersecurity courses, has authored two textbooks, and it has spoken at a lot of cybersecurity conferences. He is usually achieved by electronic mail at howard@howardposton.com or by way great post of his website at .
The wide array of components and working procedure versions in use suggests that it's extremely hard to guarantee the emulator will behave in exactly the same way for a Actual physical copy from the simulated hardware and application. This is certainly especially true when the device’s digital camera or fingerprint scanning technological innovation is linked to the test.
Google Gruyere: Google builders designed this Website app, named for the cheese, loaded with vulnerabilities for any person to hack securely.
This permits your Corporation To guage its security functions including fingerprinting or camera factors that buyers ought to interact with to use the application. Pen examination teams also needs to assess how the applying will behave based upon its recent working system (OS).
 Rider Strong Then & Now!
Rider Strong Then & Now! Michael Bower Then & Now!
Michael Bower Then & Now!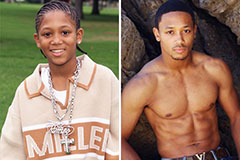 Romeo Miller Then & Now!
Romeo Miller Then & Now!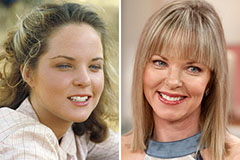 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!